Jun 26, 2017
Here's a short guide to setting up a VPN on Linux — specifically Private Internet Access on a Raspberry Pi, because I'm mostly writing this as a reminder to myself — with a kill switch to prevent non-VPN traffic. I'm targeting a Pi 3 with Raspbian Jessie here, but the procedure should be similar for other machines and distros as long as packages like OpenVPN and UFW are available.
OpenVPN setup
- Physical access to your Raspberry Pi should be controlled (only you) access to /etc should be restricted to the user that OpenVPN is running under the files with.key are TOTALLY SECRET the certificate.crt or.crs – are to be sent, lost, revoked – could be always renewed.
- Private Internet Access is the leading VPN Service provider specializing in secure, encrypted VPN tunnels which create several layers of privacy and security providing you safety on the internet. Our service is backed by multiple gateways worldwide with access in 30+ countries, 50+ regions.
- This video walks you through how to setup a persistent VPN connection to your Private Internet Access PIA VPN provider. It will reconnect on reboot.Below are.
- Private Internet Access is the leading VPN Service provider specializing in secure, encrypted VPN tunnels which create several layers of privacy and security providing you safety on the internet. Our service is backed by multiple gateways worldwide with access in 77+ countries, 100+ regions.
There are quite a few various scripts that in some way install openvpn for you. This project, in particular, was started by 0-kaladin and began from the code by StarshipEngineer to help to install OpenVPN on a raspberry pi as simple as it can be.
Install OpenVPN.
Download the VPN provider's OpenVPN configuration files. For PIA, this usually means this one.
OpenVPN on Linux uses .conf for config files instead of .ovpn, so rename them accordingly.
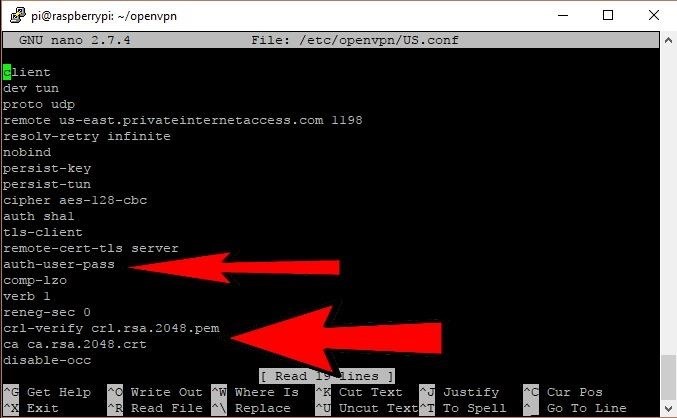
To enable automatic authentication when connecting, put your VPN username and password in a file next to the configs.
It's not very secure, so add a little protection by limiting access to the owner.
Next, make the configurations refer to this file by appending some directives at the end of each. Here I'll also throw in a couple of quality tweaks such as keepalive, logging to make troubleshooting easier, and automatic execution of a script called update-resolv-conf, which might be necessary for DNS resolution to work correctly when turning the VPN on and off. On Debian, this script is included in the OpenVPN install.
From here, it might make sense to continue as root. Move everything into place by copying the auth file, configurations, certificate and key file to /etc/openvpn.
To make OpenVPN automatically connect with a certain configuration, set the AUTOSTART directive in /etc/default/openvpn to the configuration filename without the extension.
Note 2020-03-14: since this post was first published, there's a better way to run OpenVPN as a service. Instead of using /etc/default/openvpn, move all the configuration files one level down into /etc/openvpn/client and enable the service by calling systemctl enable openvpn-client@Germany. I've tested this on Raspbian Buster, but I'm unsure if it works on older versions as well.
It should now be possible to start up OpenVPN and have it connect.
To verify this, wait a few seconds and run ifconfig. There should be an interface called tun0 or similar (for tunnel), which is the VPN interface. To test connectivity, call an IP echo service such as ipinfo.io, which should report an IP and a country matching your configuration.
UFW kill switch
At this point, if the VPN connection drops or OpenVPN stops for some reason, your machine will talk freely over your regular, non-VPN interface. Depending on the use case, it might be preferable for it to stop communicating completely instead, like if you're downloading warez concerned about your privacy.
To ensure this, we're going to set up a firewall to deny everything but the VPN handshake on the regular interfaces eth0 and wlan0 while placing no restrictions on tun0. I'm going to use UFW because it's fairly intuitive compared to iptables.
Next we fill in the firewall rules. First, allow everything on OpenVPN's network interface.
OpenVPN obviously needs to be able to connect on the regular interface, and with the default PIA configuration files, this means allowing
- DNS resolution on port 53 to find e.g.
germany.privateinternetaccess.com - The actual VPN port specified by the configuration files, i.e. 1198
You might also want to have the machine reachable from the local network to SSH into it and such, so allow everything to those IPs. My local network has IPs in the 192.168.0.* range so I'll be using that.
Finally, block everything else and enable the firewall.
Now test this by stopping OpenVPN and sending a request:
Because DNS is allowed outside the VPN, ipinfo.io is resolved, but the request times out after 5 seconds because port 80 is blocked. Turning OpenVPN on again restores connectivity.
And that's basically it. Easy, right? Not really, but it works fairly well.
In this ./note I am going to show you how set up the VPN connection provided by Private Internet Accessin Raspberry PI (but the same steps are valid for any other Linux distribution).
I found these instruction in the Private Internet Accessforum (https://www.privateinternetaccess.com/forum/).

1. If you don't have done this already, you need to install OpenVPN.
sudo apt-get install openvpn
2. Move to the OpenVPN directory in /ect:
cd /etc/openvpn
3. Download from the Private Internet Access website the zip folder. This folder contains all the config files for OpenVPN.
wgethttps://www.privateinternetaccess.com/openvpn/openvpn.zip
4. Unzip the folder using unzip. If you don't have unzip already installed in your system run the following command:
Free Vpn For Raspberry Pi
sudo apt-get install unzip
and then unzip:
sudo unzip openvpn.zip
5. In order to see the list of servers to which you can connect run:
ls -l

To make OpenVPN automatically connect with a certain configuration, set the AUTOSTART directive in /etc/default/openvpn to the configuration filename without the extension.
Note 2020-03-14: since this post was first published, there's a better way to run OpenVPN as a service. Instead of using /etc/default/openvpn, move all the configuration files one level down into /etc/openvpn/client and enable the service by calling systemctl enable openvpn-client@Germany. I've tested this on Raspbian Buster, but I'm unsure if it works on older versions as well.
It should now be possible to start up OpenVPN and have it connect.
To verify this, wait a few seconds and run ifconfig. There should be an interface called tun0 or similar (for tunnel), which is the VPN interface. To test connectivity, call an IP echo service such as ipinfo.io, which should report an IP and a country matching your configuration.
UFW kill switch
At this point, if the VPN connection drops or OpenVPN stops for some reason, your machine will talk freely over your regular, non-VPN interface. Depending on the use case, it might be preferable for it to stop communicating completely instead, like if you're downloading warez concerned about your privacy.
To ensure this, we're going to set up a firewall to deny everything but the VPN handshake on the regular interfaces eth0 and wlan0 while placing no restrictions on tun0. I'm going to use UFW because it's fairly intuitive compared to iptables.
Next we fill in the firewall rules. First, allow everything on OpenVPN's network interface.
OpenVPN obviously needs to be able to connect on the regular interface, and with the default PIA configuration files, this means allowing
- DNS resolution on port 53 to find e.g.
germany.privateinternetaccess.com - The actual VPN port specified by the configuration files, i.e. 1198
You might also want to have the machine reachable from the local network to SSH into it and such, so allow everything to those IPs. My local network has IPs in the 192.168.0.* range so I'll be using that.
Finally, block everything else and enable the firewall.
Now test this by stopping OpenVPN and sending a request:
Because DNS is allowed outside the VPN, ipinfo.io is resolved, but the request times out after 5 seconds because port 80 is blocked. Turning OpenVPN on again restores connectivity.
And that's basically it. Easy, right? Not really, but it works fairly well.
In this ./note I am going to show you how set up the VPN connection provided by Private Internet Accessin Raspberry PI (but the same steps are valid for any other Linux distribution).
I found these instruction in the Private Internet Accessforum (https://www.privateinternetaccess.com/forum/).
1. If you don't have done this already, you need to install OpenVPN.
sudo apt-get install openvpn
2. Move to the OpenVPN directory in /ect:
cd /etc/openvpn
3. Download from the Private Internet Access website the zip folder. This folder contains all the config files for OpenVPN.
wgethttps://www.privateinternetaccess.com/openvpn/openvpn.zip
4. Unzip the folder using unzip. If you don't have unzip already installed in your system run the following command:
Free Vpn For Raspberry Pi
sudo apt-get install unzip
and then unzip:
sudo unzip openvpn.zip
5. In order to see the list of servers to which you can connect run:
ls -l
6. As you can see each server config file has .ovpn extension. Now you can run the final command to connect to the server:
sudoopenvpn config-sever-filename.ovpn
Once the previous command is executed you are required to insert your username and password of your Private Internet Access account. If you want to avoid to insert username and password every time you want to connect to the VPN you can follow these steps:
1. Create a .txt file in the /etc/openvpn folder (same folder of the .ovpn file) . You can name this file ‘pass.txt‘
2. In the first two lines of the file put your username and password, like:
username
password
Pia Vpn On Raspberry Pi
3. Save and close the file.
4. Open up your .ovpn and add the following line at the bottom:
auth-user-pass pass.txt
5. Save and try to connect again. You should not be required to insert username and password this time.
That's it.
In a next post I will show how to connect automatically to the VPN at boot.
